Zero trust and best practices in an IT shop with Windows client devices have practical rules on avoiding local administrator access, there are still legitimate reasons to need that access. There are several ways to accomplish this, but often implemented with overlapping configurations and overprivileged to many IT staff and users.
If your organization is required to align with the Cybersecurity Maturity Model Certification (CMMC) Program (https://dodcio.defense.gov/cmmc/About/), your application and documentation of these options are critical. Regardless of being in GCC Moderate, GCC High, or which level of CMMC, this should be at the top of your list along with Conditional Access Policies.
In this post, we’ll focus on the capabilities currently available with Entra ID and Intune.
Table of Contents
- Local user group membership via Command Line
- Local administrators group on Microsoft Entra joined devices
- Local user group membership with Intune
- Windows Local Administrator Password Solution in Microsoft Entra ID
- Which solutions is right for me?
Local user group membership via Command Line
This approach is handy if you need to add a given user local admin to a given Windows client. You see this frequently if the user is a developer, IT engineer, or other user that needs local admin rights permanently on that device, or perhaps a short period of time.
Here is an example of how to add a user to the local administrators group via command line:
# Note: AzureAD is always the prefix before \UserUpnnet localgroup administrators /add "AzureAD\UserUpn"Here is an example of how to add a user to the local administrators group via command line:
# Note: Contoso is the domain namenet localgroup administrators /add "Contoso\username"This is NOT recommended as a regular practice for device management. https://learn.microsoft.com/en-us/entra/identity/devices/assign-local-admin#manually-elevate-a-user-on-a-device
CMMC Note: Enabling direct local admin support for given users on a device that interacts with CUI based information is not recommended. It would allow that user to make configuration changes that could impact the security and compliance requirements.
Local administrators group on Microsoft Entra joined devices
As devices join Entra, we can configure specific users and groups to also be local administrators. This can work in combination with Entra Privileged Identity Management, but that needs both a license and configuration to make the best use of it.
If you’re using Microsoft 365 Business suite licensing, then you don’t have this unless those users that would use PIM have an additional license (e.g. Entra ID P2). Let’s say you don’t have licensing for PIM, then local admin assignment by defining which users are in the Device Management role, or you can directly assign by user but that’s not recommended), is your option here. https://learn.microsoft.com/en-us/entra/identity/devices/assign-local-admin
This option will impact all devices within the tenant.
CMMC Note: It’s recommended that any IT staff (including outsourced services like an MSP) have named accounts with licensing and configuration of PIM be required. This ensures an audit trail for access is maintained and elevation of privilege is required accordingly.
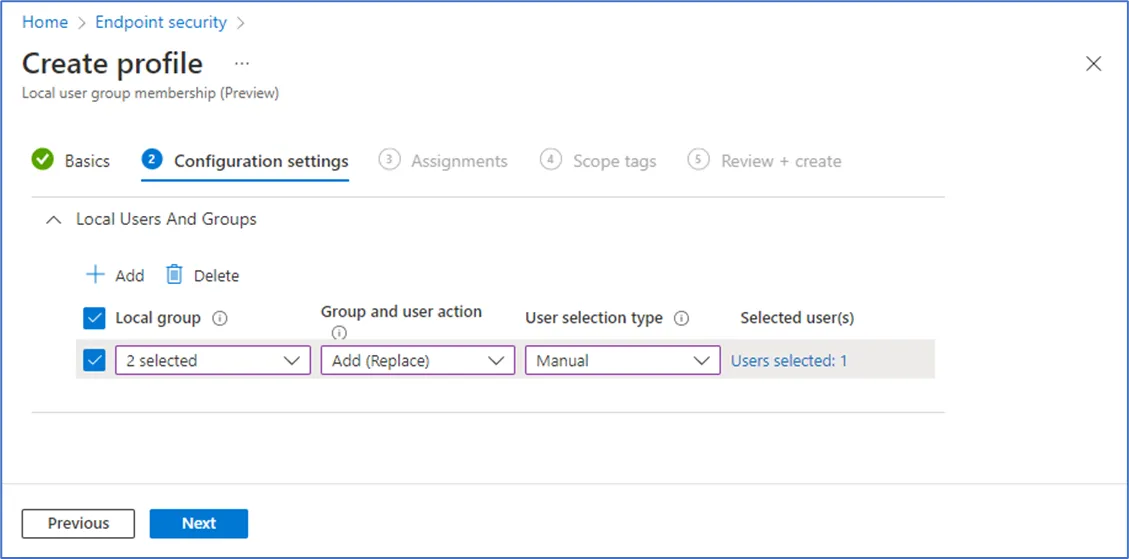
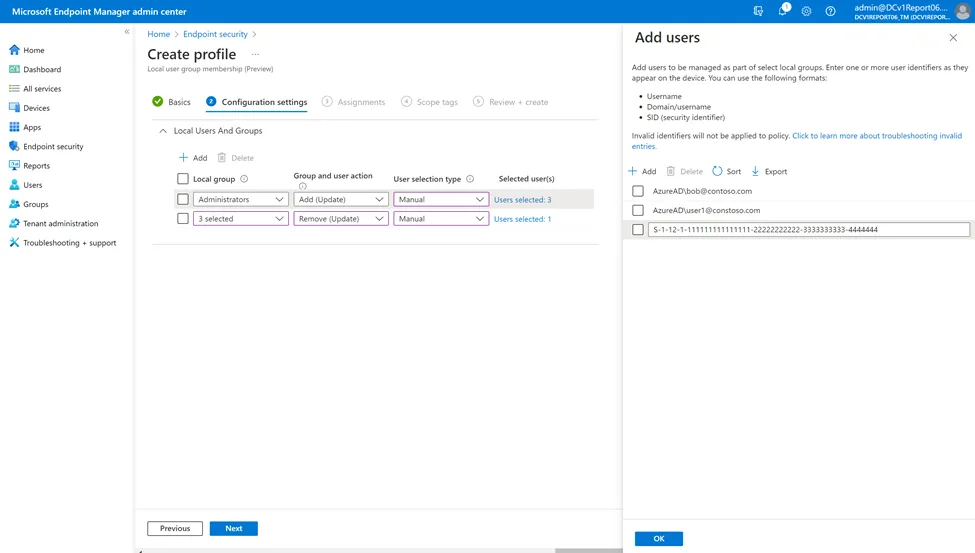
Local user group membership with Intune
If you have Intune managed devices, you can create a configuration policy via Account Protection that defines which users or group of users to be added to a given local group (in this case Administrators). https://learn.microsoft.com/en-us/mem/intune/protect/endpoint-security-account-protection-policy#manage-local-groups-on-windows-devices This option can be scoped to specific devices. You’d need to create a policy and associated security group that targets the devices you want to target. This would support having specific IT staff to be listed in the policy and target devices based on the security group.
The following link provides additional information on using this type of policy: https://learn.microsoft.com/en-us/entra/identity/devices/assign-local-admin#manage-administrator-privileges-using-microsoft-entra-groups-preview
One important note found in the link above is: Managing local administrators using Microsoft Entra groups isn’t applicable to Microsoft Entra hybrid joined or Microsoft Entra registered devices.
I’m thinking it’s because:
- Microsoft Entra hybrid joined: Leverage Local Active Directory based access
- Microsoft Entra registered devices: Probably a BYOD and thus being a local admin for a personal computer isn’t what we’d want
Windows Local Administrator Password Solution in Microsoft Entra ID
The good news is that the Windows Local Administrator Password Solution (LAPS) is included in all tiers of Entra ID! This will enable Entra IT to manage and store the local admin password (including rotating passwords) across all of your Windows clients.
Configuration of this is pushed either via an Intune policy, Group Policy, or local device policy (in case you don’t have an Intune license or local Active Directory).
https://learn.microsoft.com/en-us/entra/identity/devices/howto-manage-local-admin-passwords
If you followed previous best practices of disabling or renaming the local administrator account, you’ll need to undo that. Or you can use a new local username but you’ll have to create that before you enable LAPS and tell LAPS of that account.
CMMC Note: With LAPS, the local administrator password is stored in Entra ID and I’m sure that will give you pause. However, it rotates the password, audit log of who/when accessed it, and then resets it after a configured period of time as you define.
Which solutions is right for me?
The answer is probably a combination depending on your organizational structure (different IT teams), environment (cloud only or hybrid), and licensing.
At the very least, I highly recommend deploying Windows LAPS. It’s free and easy to manage which I previously posted on. It’s a great way to manage local admin passwords across all your Windows clients.